Single Sign On User Login
In this guide, we show you how to connect your Microsoft Azure account to Survey Booker to enable Single Sign On. Single Sign On helps you to control user access to all apps from one place. If you revoke user access in Azure, your surveyor/office users will not be able to log in as their login will not be authorised.
Single Sign On is only applicable for surveyor/office users. Introducers and customers log in as normal using an email and password.
Connecting Microsoft Azure
In your user settings (Settings > User settings > Manage users), you will see a slider button. Click on it and it will turn blue confirming Single Sign On is turned on.
Once it is on, any surveyor/office user logging in will be redirected to Azure after entering their email address.
After successful login, the user is redirected back to Survey Booker to continue as normal.
Disconnecting Microsoft Azure
Click on the blue Single Sign On slider button and a pop-up message will appear asking if you are sure.
Once you confirm, it will turn off and users will be required to log in with an email and password.
Connecting Azure for the first time
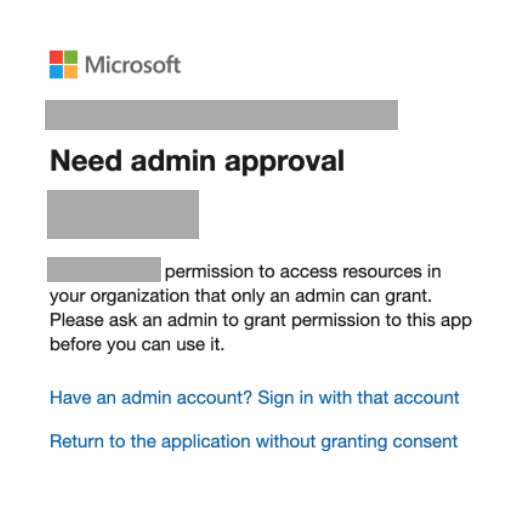
The first time you connect to Azure, the user signing in must use an administrator level account on your Azure account. This is required to approve the connection with the Survey Booker app.
If your email is not administrator level you will see this error:
To resolve this, an Administrator needs to configure user consent settings in Azure.
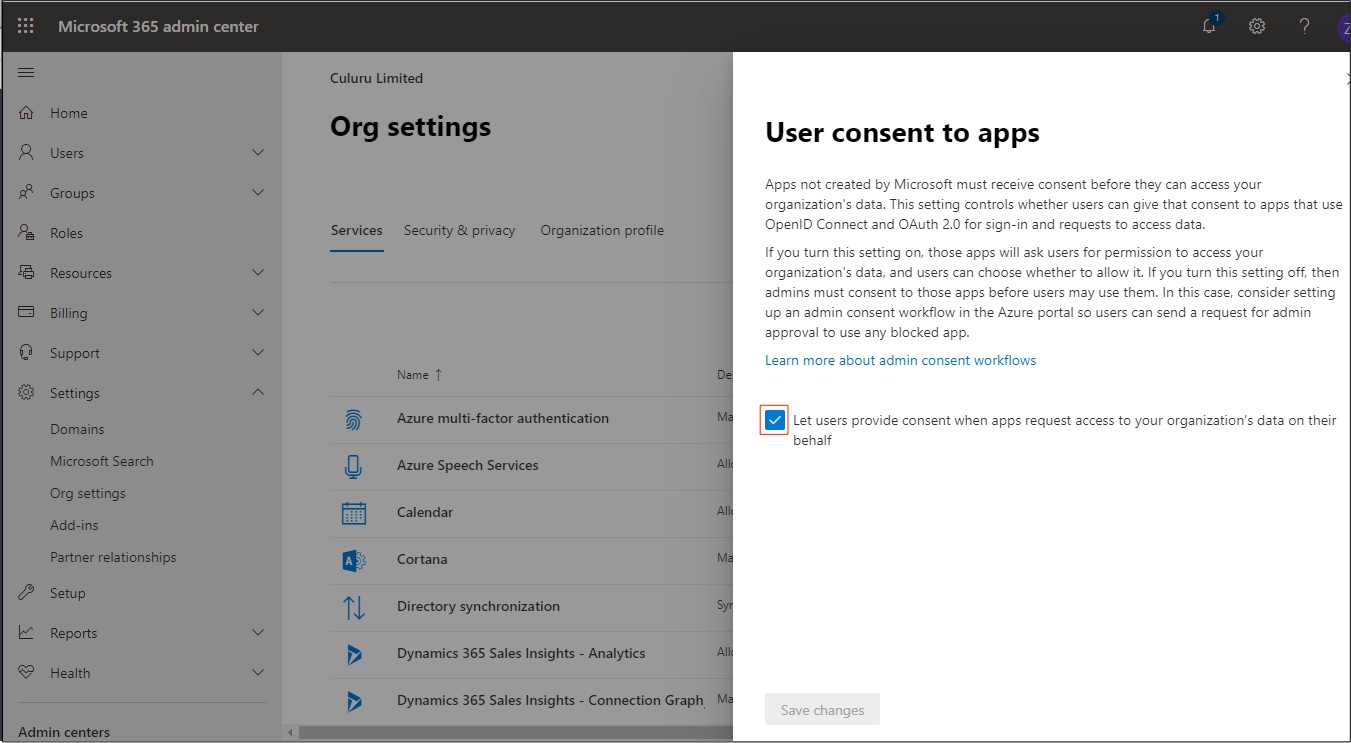
Configure User Consent Settings
1. Sign into your Azure administrator account.
2. Click Settings > Org Settings.
3. In User consent to apps, ensure checkbox is ticked.
4. Click Save Changes.
An alternative to the above configuration is to consider enabling the admin consent workflow to allow users to request an administrator’s review and approval of an application that the user is not allowed to consent to:
Further information about the admin consent workflow can be found on Microsoft’s website here: https://docs.microsoft.com/en-
Alternatively you can grant tenant-wide admin consent to an application: https://docs.
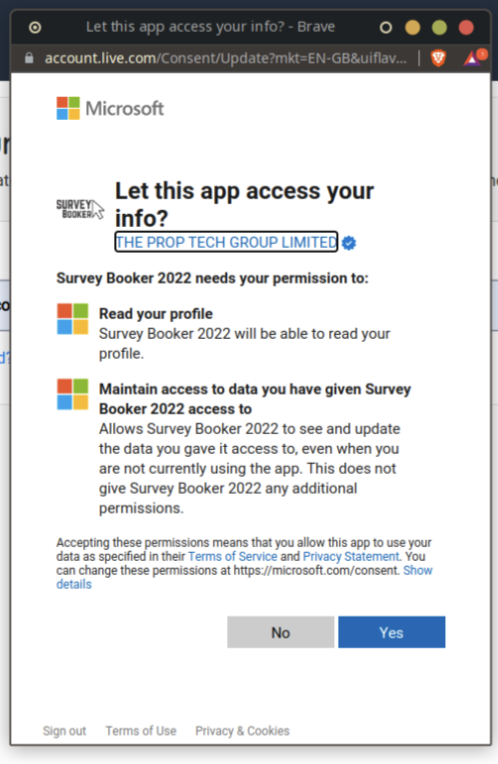
Admin user
Once you sign in with an administrator level Azure user, you’ll be asked to grant permission to Survey Booker to read your profile and to see and maintain data we have access to (your profile).
Once you approve access, you’ll be redirected to Survey Booker.
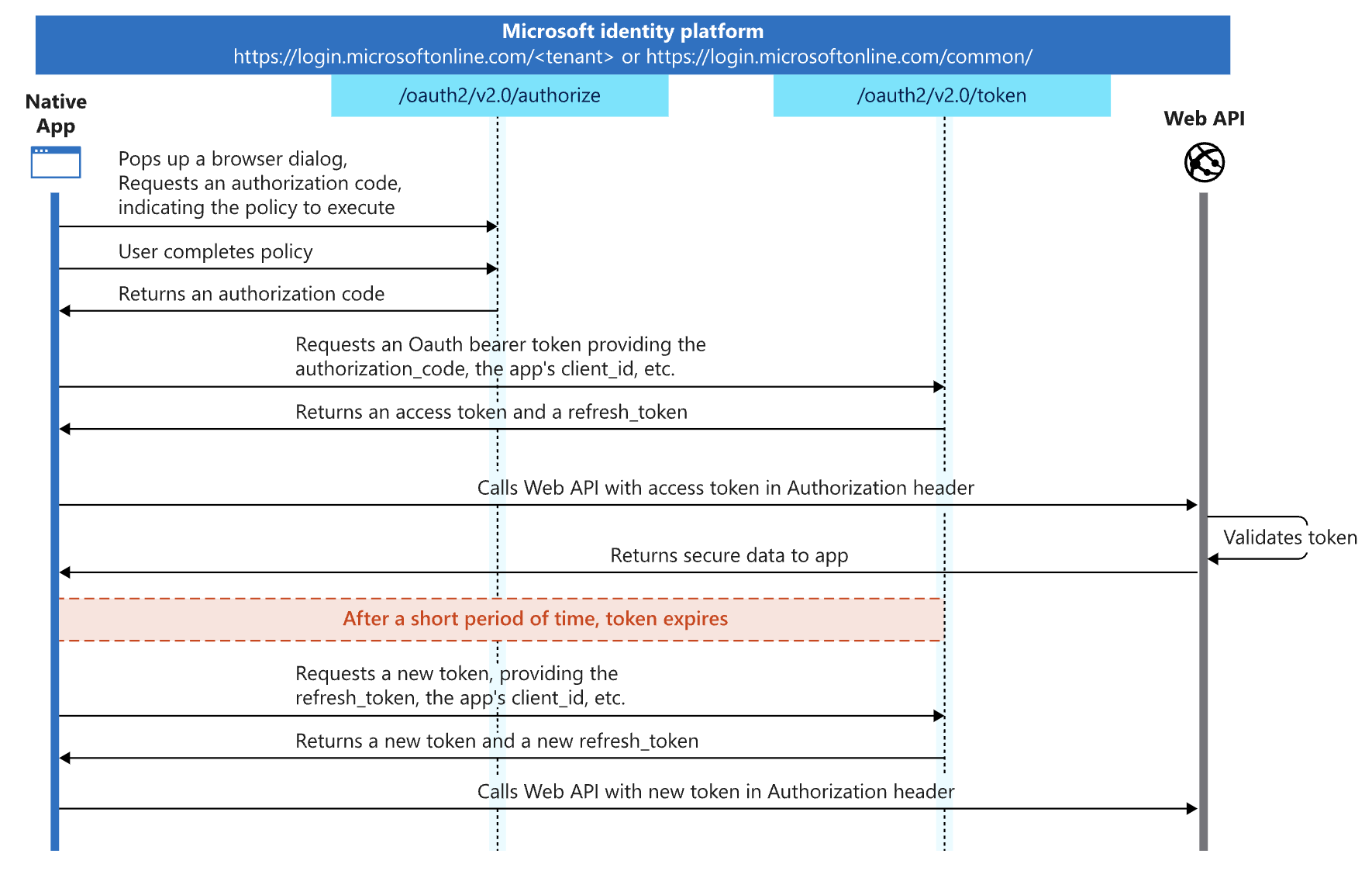
The technical bits
We connect to Azure using OAuth 2.0 Authorization code flow (with PKCE).
- The authorization code flow allows the application to exchange an authorization code for ID tokens to represent the authenticated user and Access tokens needed to call protected APIs.Proof Key for Code Exchange, or PKCE, is an extension to the authorization code flow to prevent authorization code injection attacks. This IETF standard mitigates the threat of having an authorization code intercepted and enables secure OAuth exchange from public clients as documented in RFC 7636. In addition, it returns refresh tokens that provide long-term access to resources on behalf of users without requiring interaction from those users.Using the authorization code flow with PKCE is the more secure and recommended authorization approach, not only in native and browser-based JavaScript apps, but for every other type of OAuth client.